Educate Users and Implement Secure Systems
Security Policy Development
Security policies provide a documented framework for an organization’s cyber strategy and create effective administrative, technical and physical protocols to reduce the risk of cyberattacks.
Protect People and Information
Security Policy Development
“If you can’t see it, you can’t defend against it.™"
Security policies provide a documented framework for an organization’s cyber strategy and create effective administrative, technical and physical protocols to reduce the risk of cyberattacks. Cybersafe's Security Policy Development service includes 19 customized security policies.
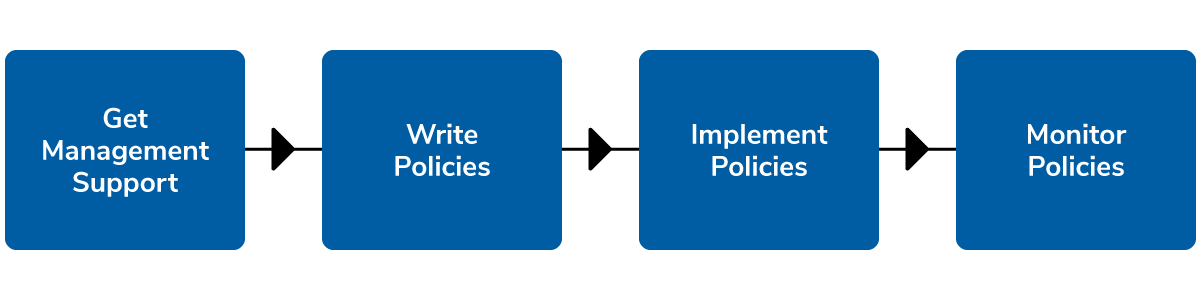
Cybersafe provides a framework for keeping your organization’s overall security posture at a reasonable and appropriate level.
In order to design and implement an effective security program, your team must have an ongoing strategy that incorporates a top-down approach. No matter how large or small your company is, a good Written Information Security Program (WISP) paints a big picture of how best to protect your company’s sensitive data.
There are 5 key components of a comprehensive WISP:
Want to learn more? Download the factsheet (PDF)
1. Designated Security Officer
Regulated industries are required to have a designated security officer in place who's responsible for coordinating and implementing your security program.2. Risk Assessment
This component assesses the risks your organization faces and what reasonable and appropriate steps need to be taken in order to mitigate them. This assessment allows you to prioritize and apply cost-effective countermeasures.3. Policies & Procedures
Once the risk assessment is completed, a written document that states how a company plans to protect its digital assets is developed. This is a living document that is continuously updated as technology and employee requirements change.4. Security Awareness Training
The human factor is the weakest link in the security chain. All employees need to be aware of their roles and responsibilities when it comes to security. Users need to have ongoing security awareness training to protect against social-engineering attacks.5. Regulatory & Audit Compliance
Organizations may need to comply with federal and state regulatory standards such as HIPAA, PCI, GLBA, Sarbanes-Oxley, and FISMA. Periodic audits are necessary to assess the level of security in place, whether it’s been breached, and to also make sure it complies with your security program.19 types of Security Policies
- Acceptable Use Policy
- Backup Policy
- Confidential Data Policy
- Data Classification Policy
- Email Policy
- Encryption Policy
- Guest Access Policy
- Incident Response Policy
- Mobile Device Policy
- Network Access Policy
- Network Security Policy
- Outsourcing Policy
- Password Policy
- Physical Security Policy
- Remote Access Policy
- Retention Policy
- Third-Party Connection
- VPN Policy
- Wireless Access Policy
Benefits of Security Policies
- Set the behavioral rules for users, system administrators, management, and security personnel.
- Authorize security personnel to monitor, probe, and investigate.
- Define and authorize the consequences of violation.
- Help minimize risk and exposure.
- Help track compliance with regulations and legislation.
Security Policies are living documents that are continuously updated and changing as technologies, vulnerabilities and security requirements change.

Expertise
Why Cybersafe?
Cybersafe’s team of cyber experts have developed and implemented hundreds of Written Information Security Programs (WISPs) in both the public and private sectors.
A holistic approach
The Cybersafe Difference
While many security policies share common themes, we understand that each organization is unique and must develop its own set of policies customized to its distinct way of conducting business.
Learn About Our Mission

